 Directory server
Directory serverIn the Domain section of the Connector settings panel you define the directory (LDAP/AD) settings of the current connector, and the generation of the directory group graph. All fields in this section are mandatory.
[ Expand All | Collapse All ]
The Directory server group of functions contains the following fields:
![]() In this field you must enter the DNS name or IP address of the directory server (LDAP/AD) used by the current connector for looking up domain information such as mail file and group membership for authorized DME users. You can specify a non-standard port by adding a port number (:<port>). On Domino, it will always search the entire LDAP tree from the root.
In this field you must enter the DNS name or IP address of the directory server (LDAP/AD) used by the current connector for looking up domain information such as mail file and group membership for authorized DME users. You can specify a non-standard port by adding a port number (:<port>). On Domino, it will always search the entire LDAP tree from the root.
![]() In this field you must enter the DNS name or IP address of the Active Directory Domain Controller used by the current connector for looking up domain information such as mail file and group membership for authorized DME users.
In this field you must enter the DNS name or IP address of the Active Directory Domain Controller used by the current connector for looking up domain information such as mail file and group membership for authorized DME users.
You must use a certain syntax, which is as follows. For performance reasons, we recommend reading from a domain controller designated as Global Catalog Server. This is done by specifying gc://.
Read from absolute AD root:
gc://[DomainController][:port]/
Note the trailing slash, which means that the entire tree will be searched from the root.
Read from specific AD container:
gc://[DomainController][:port]/DC=Users,DC=company,DC=com
In this example, the search will be targeted to the Users container.
LDAP versus GC:
If you do not use a Global Catalog, you can prefix the domain controller path with ldap:// instead of gc://.
A disadvantage of using ldap is that you risk slower performance or no response at all, depending on your AD configuration.
GC on the other hand, doesn't support users changing password using the DME client. Furthermore, it does not support the password expiration date calculation, so users cannot be warned about Days before to show expiration warning in the DME clients. If these functions are wanted, LDAP should be used.
Note that if you use secure connections, you can use the following syntax: gcs:// or ldaps://.
If you do not specify either gc:// or ldap://, it will default to using the domain name root of the domain controller that you specify. For instance, ad1.company.com. This will enable you to search from this domain down; you will be unable to search up through the specified domain.
In this field you enter the name of the user which performs the directory lookups on behalf of the DME users. For more information about creating this user, see the separate Domino and Exchange Integration documentation issued by Soliton Systems. This user should have access to querying the directory for information such as mail file location and group memberships. By convention, this user is most often named DME_Server and called the server user or technical user.
In this field you specify the password of the directory query user specified above.
One LDAP repository can refer to other LDAP repositories for information. This is especially the case for Active Directory environments. By default, DME allows this, but in some cases it may not be desirable. If you disable this field, DME will only search for information in the LDAP specified above, and not follow any chain of LDAP referrals.
Click this button to verify that the connection to the LDAP server can in fact be established with the connection information you have entered for this connector. You should do this before clicking Save. Note that the function only tests the LDAP specified in the Domain info LDAP server field, and not all LDAP servers that this DME server can reach. This way, you can test the connection against one connector at a time.
Enter the name of a user that you know exists in the LDAP directory. DME suggests the DME query user, but you for instance enter your own user name.
Click Test. If the connection to LDAP is successful, the result page will show various information about the user, retrieved from LDAP. If the connection failed, the result page will show an exception which may help you pinpoint the problem.
Click Back to try with another user, or click Cancel to end the test.
The User groups (group graph) group of functions contains the following fields:
The DME server requires a group graph, which is a tree representation of the directory groups from the organization's directory server (LDAP/AD). This graph is used by DME to detect the rights of a given user, based on the user's association with a group: is the user member of a group which is a member of DME_User (or a group impersonating DME_User - see Access rights below), of DME_Superuser, or DME_Admin. For more information, see The group graph.
Furthermore, the groups in the group graph can be used for grouping devices in the Devices tab. For more information, see Groups.
Only one system-wide group graph can be used by the DME server. It is sufficient to let one connector read out the group graph from the directory and send it to the server. Letting more connectors do this is also allowed, but not recommended. The connector used for authentication uses the group graph stored on the DME server to verify that a user is member of the DME_User group. When this field is selected, the current connector will extract the group graph from the directory server specified in the field Domain info LDAP server above, and send it to the DME server when you click Save. The group graph is extracted according to the specifications below.
In these fields you can specify the extent to which you want to send the directory group graph to the DME server. This is only relevant if the field Read out group graph above is also selected.
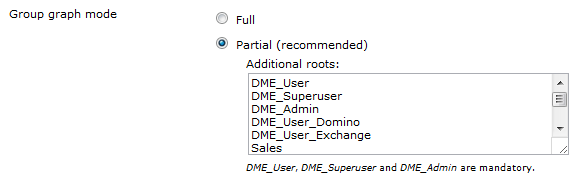
If you choose Full, all groups in the directory are included in the group graph. Choosing Full allows you to build Analyzer reports using the directory groups as parameter. However, if your organization's directory contains a very large number of groups (10,000+), it is recommended to choose Partial, as building the group graph can put quite a strain on the connector.
If you choose Partial, the DME groups DME_User, DME_Admin, DME_Superuser and their subgroups are included in the graph by default. However, you can enter additional roots to be traversed. If, for example, you enter OtherRoot as in the example shown above, the group graph will consist of the mandatory DME groups and any directory groups below OtherRoot. You can add roots that do not exist in the directory specified in the LDAP server group of fields above, for instance if you want to allow users, who are not members of any group in the specified LDAP server, to log on.
Furthermore, you can choose Partial and add the * keyword to the list. This means that all groups will be included (as in Full), with the addition of any other groups you need to specify.
When you click Save, the connector will read out the group graph and send it to the DME server. A log entry in the System category with the text New group graph arrived:, followed by the actual group graph, will be written to the log (see Log). The group graph can be seen by clicking Show directory groups in the page menu of the Server tab.
In this field you can enter the number of minutes for which the connector should try to read the directory group graph. After the specified number of minutes, the process will stop. Recommended value: 60 minutes.
In this field you can either enter the number of minutes that should pass between each refresh of the directory group graph, or you can enter a specific time of day in hh:mm format, and DME will then refresh the directory group graph at that time. You could for instance specify that DME should refresh the user/group memberships every night at 03:00.
When you have specified the LDAP server or altered the group graph setup, you can click the Test readout button to verify your changes. This button is available if the field Read out group graph is selected. If it is not (if the current connector is not used for reading out the group graph), you can enable the field, test the group graph, and then disable the field again - enabling the group graph function for the connector does not take effect until you click Save in the Domain panel.
The test verifies that the group graph can in fact be read from the LDAP server with the information specified in the LDAP server group of fields above. A popup window shows either the group graph as defined in this group of functions (as an indication of success), or an error message as an indication that the connection to the LDAP server failed. Perform the test before saving your changes to the connector. The picture below shows an example of a successful readout of the group graph.
Click Close to exit to the Domain panel again.
If you have made changes that you want to apply before the next scheduled run of the group graph readout, you can also use the Test readout function as a manual refresh of the group graph. Run the test, and click Save to save the group graph.
The Access rights group of functions contains the following fields:
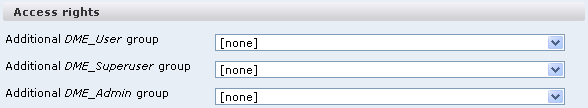
If you want to use an LDAP group in addition to DME_User for DME users, choose an LDAP group here. This group will then have the same rights as DME_User. For more information about user groups, see About users.
The functionality of this field is similar to that of the field Additional DME_User group above, but applies to the DME_Superuser group.
The functionality of this field is similar to that of the field Additional DME_User group above, but applies to the DME_Admin group.
The Supported users group of functions lets you specify which users should be serviced by the current connector (the route users) - either manually or by letting the connector broadcast for users to be serviced.
If you have a central directory server and a local mail server for a specific office/location, you can for instance configure a specific group in your directory for users of this office/location, and configure a DME connector to service users of this group only.
DME user domain
![]() You can limit the connector to only serving users from a specific domain. This allows you to run one DME server for multiple domains. For instance, if your DME server hosts users from multiple distinct companies, you can set up one connector per company by only allowing the connector to create routes to users from a certain domain only.
You can limit the connector to only serving users from a specific domain. This allows you to run one DME server for multiple domains. For instance, if your DME server hosts users from multiple distinct companies, you can set up one connector per company by only allowing the connector to create routes to users from a certain domain only.
The domain must be entered on the form domain.com. For Domino users, this must match the e-mail address of the user. For Exchange users, this must match the UserPrincipalName.
For instance, if domain.com is entered here, a user logging in as john.doe@domain.com can be serviced by this connector; a user logging in as john.doe@example.com cannot.
Route users
The users' route to a DME Connector is based on a built-in priority, where the more specific user selection has the higher priority. For instance, if a user is specified in the Users field of one connector, but is also found as member of a group specified in the Members of field of another connector, then the route will be created to the connector where the user is specified directly. If the user is not found in either of those fields of any connector, the route will be created to a connector set to Automatic (broadcast).
In this field you can specify a comma separated list of users that should be serviced by this connector. The users should be specified as they would be displayed in the User column in the Devices tab. A list could for instance be NIF,LL,MFB. In this case, only the users NIF, LL, and MFB would be serviced by this connector. This could for instance be used for debugging purposes in connection with the setup of a new DME connector.
In this field you can specify a group from the directory specified in the field Domain info directory server above. The effect is similar to that of the field Users above, and should only be used in the same circumstances - while testing a new installation. Only users that are members of the selected group are serviced by this connector. This only applies if the field Automatic below is not checked.
If this field is selected (default), the fields Users and Members of above are ignored. Instead, the DME server determines which users should be serviced by which connector by way of a user broadcast, as described in the section about the DME server architecture - see DME server architecture.
Note that it is a requirement that at least one connector is set to Automatic.
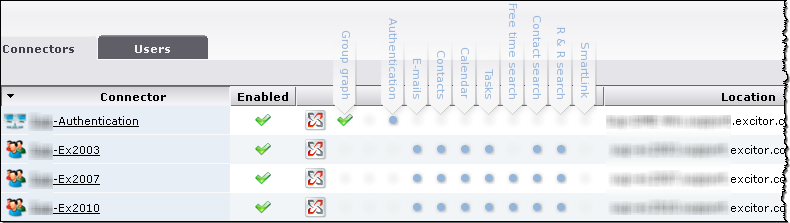
If, for instance, you use the Members of setting to route your Exchange 2003 users to one connector, your Exchange 2007 users to another connector, and your Exchange 2010 users to a third connector, then you must set up a fourth connector for Authentication only, using the Automatic setting - like this:
Click Save to save the new settings.
|
Next topic |